We pay heavy attention to the questions of safety and stability of 1С:Enterprise 8.3 in the service mode. An operation in this mode creates problems which never appeared before, when the solutions of 1С:Enterprise were operated strictly by the awarding authority. If due to the unskilled or consciously harmful configuring the application operation led to the problems, it was only the problem of the person who exploits this application solution.
When operating in the service mode, this situation is already different. A service provider who provides the services to use the application solutions on-line may have to deal not only with his own products or configurations developed by «1С» company. In addition, he may provide the services to use the application solutions developed by the other third-party providers. And, in this case, the service owner must be guaranteed from the fact that the application solution of third-party provider can disrupt either accidentally or intentionally the operation of the whole service, the operation of other application solutions published in the service.
To solve this task, we added in the server cluster a new entity – security profiles. Security profile serves in order to deny the application solution to perform the actions that can be potentially unsafe for the server cluster functioning.
The cluster administrator can assign for any information base one of the existing in the cluster security profiles. And then the potentially unsafe functionality of application solution will be limited in the range described in this profile.
Usually, after creating, the security profile denies the execution of all potentially unsafe actions:
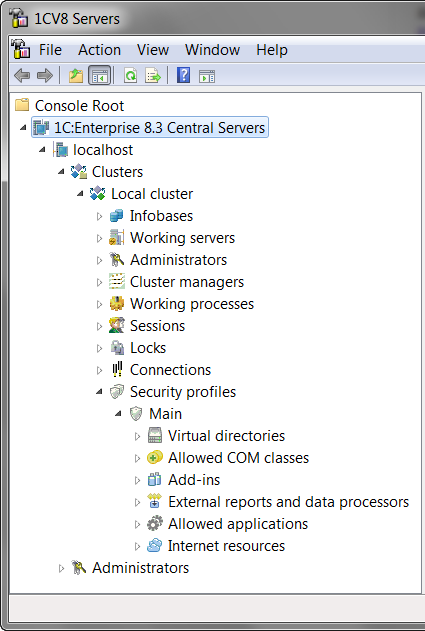
These actions are such as:
- access to the server file system;
- launch of COM-objects;
- use of 1С:Enterprise external components;
- launch of external processors and reports;
- launch of applications installed on the server;
- access to the Internet resources.
Thus, it is very simple to protect against unwanted actions of unknown application solution: it is necessary to create an empty security profile and assign it to the information base.
Further, if it is necessary, it is possible to extend this profile describing in it the actions that are permitted to be executed by the application solution.
For example, it is possible to permit the application solution to access some area of server file system. To do this, it is required to describe this resolution in the section Virtual directories:

In this case, the application solution code will operate with the logical URL, but physically the access will be performed on the server to the directory specified in the property Physical URL. During the application solution attempt to access the path other that the logical URL, an exception will be thrown.
It is possible to permit the launch and use of any COM-objects installed on the server. For example, Microsoft Excel application:

To do this, it is required to specify an identifier of COM-class Excel.Application installed on the server. This information can be obtained from the Windows system registry. If the application solution will try to use another COM-class, an exception will be thrown.
In addition, it is possible to permit the use of some 1С:Enterprise external components. For example, Full name declension:

In this case, it is required to specify in the resolution the control sum of the file of this external component. It is possible to learn it using one of the utilities available in the Internet or by writing a small piece of code in the script of 1С:Enterprise.
To permit the work with external report or processor, it is also required to specify in the resolution the control sum of the file of this report/processor:

In order to permit the application solution to launch the application installed on the server, it is required to specify the start line of this application:

So, the above example permits the application solution to launch on the server Microsoft Office Word 2007, herewith, the symbol «%» in the start line means an arbitrary sequence of characters.
Finally, it is possible to permit the access of application solution to some Internet resources:

To do this, it is required to specify the protocol with which the access will be performed and the address of site.
Thus, it is possible to permit the application solution to work with necessary resources that do not violate the required security level.
It may be known in advance, for example, that all the external components with which the application solution works are safe and do not contain the unsafe code. In this case, it is not required to create a separate permission for each of them. in the properties of security profile it is possible to permit the launch of any external components:

In this case, it will not matter what kind of permissions are set in the section External components.
Thanks to the security profiles, now it is possible to safety isolate from each other the information bases that operate in the service mode, as well as isolate from each other the areas of the same base that operate in the data separation service. In addition, the use of profiles in general increases the cluster reliability by prohibiting the potentially unsafe actions.
Another important point related to the appearance of security profiles is an ability to extend the use of safe mode for software code execution. Now it is possible for it ti permit some actions that were denied before. For example, the work with temporary files.
