
“1С” company announces the release 29.05.2013 of the final version 8.3 of “1С:Enterprise” platform.
Continue reading On the release of the final version 8.3 of “1C:Enterprise” platform

“1С” company announces the release 29.05.2013 of the final version 8.3 of “1С:Enterprise” platform.
Continue reading On the release of the final version 8.3 of “1C:Enterprise” platform

What is RLS?
RLS (Row Level Security) - restriction at the level of records in the database tables. In contrast to the delimitation of the rights base on the usage of roles that actually delimit access to the specific tables of base as a whole, RLS allows configuring an access to the specific records.
Continue reading Simple example of work with RLS
Technological log (hereinafter TL) is intended to detect the errors occurred when operating the system and to diagnose the work of technical support service of “1С” company, as well as to analyse the technical characteristics of system operation.
TL allows logging all the events of 1С:Enterprise (or their part using the filter), for example:
- executable code of 1С:Enterprise 8;
- Transact-SQL code for DBMS;
- interactive user actions;
- error messages;
- memory leaks.
Continue reading Technological log 1C:Enterprise 8 for the lazy
According to the research data of TNS in 2012, about 90% of companies in the major Russian cities used 1С products for bookkeeping.
They are followed, according to the research data, by the system BEST and «Sail» whose shares in the number of Russian companies where they are used do not exceed 1,4% and 1,2% respectively. Among the world’s leaders of ERP-system market it can be noted in the list Microsoft Dynamics NAV with a share of 0,2%.
1С representatives stated that their solutions are often used for bookkeeping also in the companies where the enterprise management systems of the world’s largest vendors are installed.
Continue reading 90% Russian companies use 1C products for bookkeeping
I want to share with visitors of the site my approach to transform the values table in the values tree and back.
In general, when developing the branch-wise task, it was necessary almost for all the documents to output information as a tree and store it in the table parts of document, as well as in the interactive data processor as a tree.
Continue reading Example of transformation from the values tree to the values table and back

What a pleasure to talk about what a wonderful system was implemented, how the costs were reduced, how equipment was modernized or what a cool server room was built. It’s nice when the big bosses com to cut the ribbons and many talk about everything. It’s nice when the news about this is printed in newspapers. It’s nice, incredible, amazing, surprising.
But we are living in Russia – we are not looking for easy ways. Maybe in other countries as well as with us, but maybe not – I don’t know, I didn’t see, didn’t implement. But I have seen a lot of different companies in Russia from inside. Here on such case will be discussed.
Continue reading Screw loose
Let’s talk about automation. Automation of enterprises, or at least some departments or even some functions. The word by itself is something artificial. It is not seen the life behind it. Sounds nice, but can be interpreted in different ways.
On the first place there is always the question – how will change the role of particular person who will work with created system? Will it be easy or hard to work, will he creatively work with the system or just push the button on command, how will change the requirements for his qualification?
Continue reading When employee becomes a gadget
 This article is a view of programmer who moved to 1С from technologies of worldwide software manufacturers — Oracle, Microsoft and others. It is intended primarily for those who makes such transition or is about to make. Some features of 1C programmer work are considered.
This article is a view of programmer who moved to 1С from technologies of worldwide software manufacturers — Oracle, Microsoft and others. It is intended primarily for those who makes such transition or is about to make. Some features of 1C programmer work are considered.
Continue reading 1C stalking
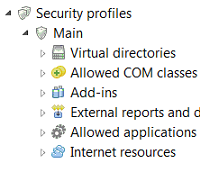
We pay heavy attention to the questions of safety and stability of 1С:Enterprise 8.3 in the service mode. An operation in this mode creates problems which never appeared before, when the solutions of 1С:Enterprise were operated strictly by the awarding authority. If due to the unskilled or consciously harmful configuring the application operation led to the problems, it was only the problem of the person who exploits this application solution.
Continue reading Security profiles in 1C:Enterprise 8.3
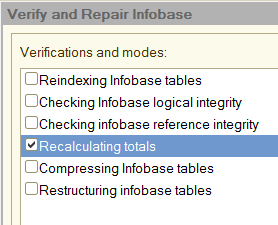
We often hear the recommendation that the recalculation of totals should be performed regularly and this operation results in the improvement of performance, but what lies behind this procedure and what problems are solved exactly?
Continue reading Why is it required in 1С to periodically recalculate the registers totals?